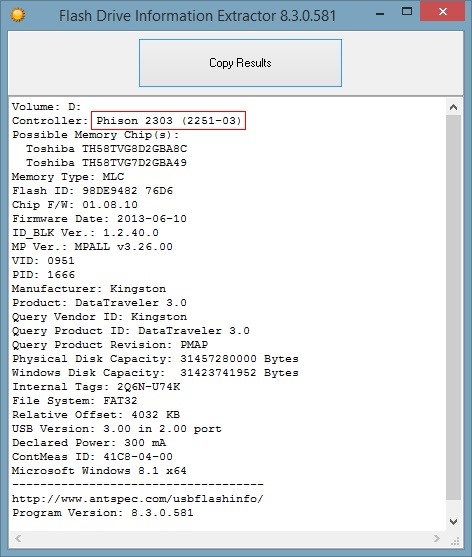
MYAMIA iPhone Serial Port Engineering Cable Dcsd USB Cable for iPhone 7 7P 8 8P X Engineering & Exploit : Amazon.de: DIY & Tools

USB Device Under Threat. New Hack Is Undetectable And Unfixable – Cyber Security Experts – Middle East | Eastern Province | Al-Khobar, Kingdom of Saudi Arabia
GitHub - mrxrobotn/USBexploit: Steal all saved browser passwords within 6 seconds using an USB exploit

USBAnywhere Vulnerabilities Found on Supermicro Servers Could Allow Hackers to Exploit Them Remotely | Cyware Alerts - Hacker News




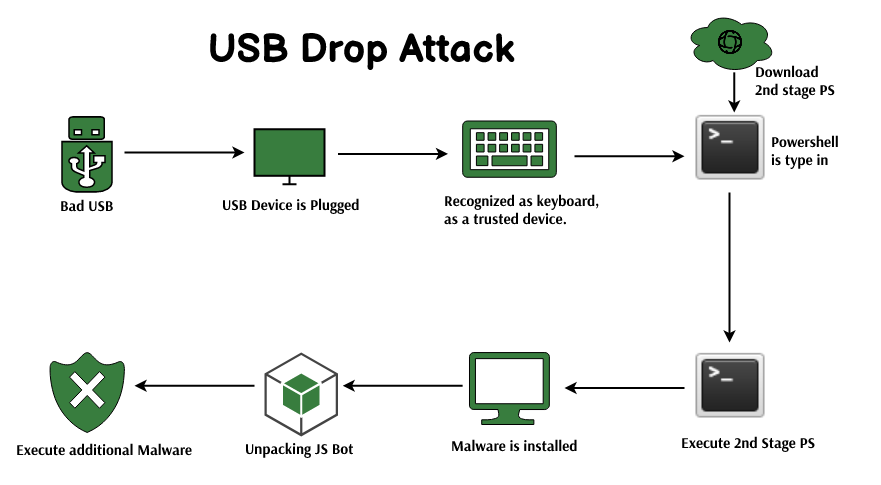









/cdn.vox-cdn.com/uploads/chorus_asset/file/18993465/omg3_800x.jpg)